🛠️ Best IoT Pentesting Tools in 2025: Flipper Zero, HackRF, Proxmark & More
So you want to get into IoT hacking?
Maybe you’ve seen flashy TikTok demos of the Flipper Zero cloning a garage door remote. Perhaps you’ve read about hackers hijacking cars through wireless key fobs. Or maybe you’re staring at your own smart plugs, cameras, and Alexa speakers, thinking, 'Are these really secure?'
That curiosity is how many people discover IoT pentesting — the practice of testing Internet of Things devices for vulnerabilities. However, the moment you start researching, it becomes overwhelming.
You find yourself asking:
- Do I need a Flipper Zero, or is it just a toy?
- What’s the difference between HackRF and LimeSDR?
- Is a Proxmark3 really necessary if I already have Flipper?
- Should I buy a multimeter, a soldering iron, or a full soldering station?
- What even is a Bus Pirate?
The gear question is where most beginners get stuck. And because many IoT pentesters are hobbyists first, it’s easy to overspend on equipment you’ll barely use.
This guide is here to cut through the noise.
I’ll walk you through:
- The Essential IoT Pentesting Tools to Start With.
- The differences between Flipper Zero, HackRF, Proxmark, soldering gear, and more.
- How to build your IoT pentesting lab on a budget (from $200 kits to $2,000+ professional setups).
- What to buy now vs later — so you don’t waste money.
By the end, you’ll have a clear roadmap for starting IoT hacking responsibly and effectively.
⚡ Why IoT Pentesting Tools Matter
The world is drowning in IoT devices. Smart locks, thermostats, fridges, cameras, cars, doorbells, drones, medical devices — billions of “things” are online.
Unfortunately, most IoT manufacturers prioritize:
- Speed to market (ship now, patch later).
- Cost-cutting (cheapest chips, weakest encryption).
- User convenience (weak passwords, auto-connect features).
This leads to massive security gaps.
Real-world examples:
- The Jeep Cherokee hack (2015): remote takeover of a moving car via its infotainment system.
- The Mirai botnet (2016): millions of insecure IoT devices turned into a DDoS army.
- Smart lock exploits: opening doors via Bluetooth flaws.
- Key fob relay attacks on cars: stealing vehicles without ever touching a key.
👉 IoT pentesting matters because these devices hold the keys to our homes, cars, businesses, and hospitals.
And if you want to pentest them, you need the right tools.
🔑 Beginner IoT Pentesting Toolkit (Under $200)
Starting IoT hacking doesn’t require thousands of dollars. With under $200, you can build a kit that covers the basics.
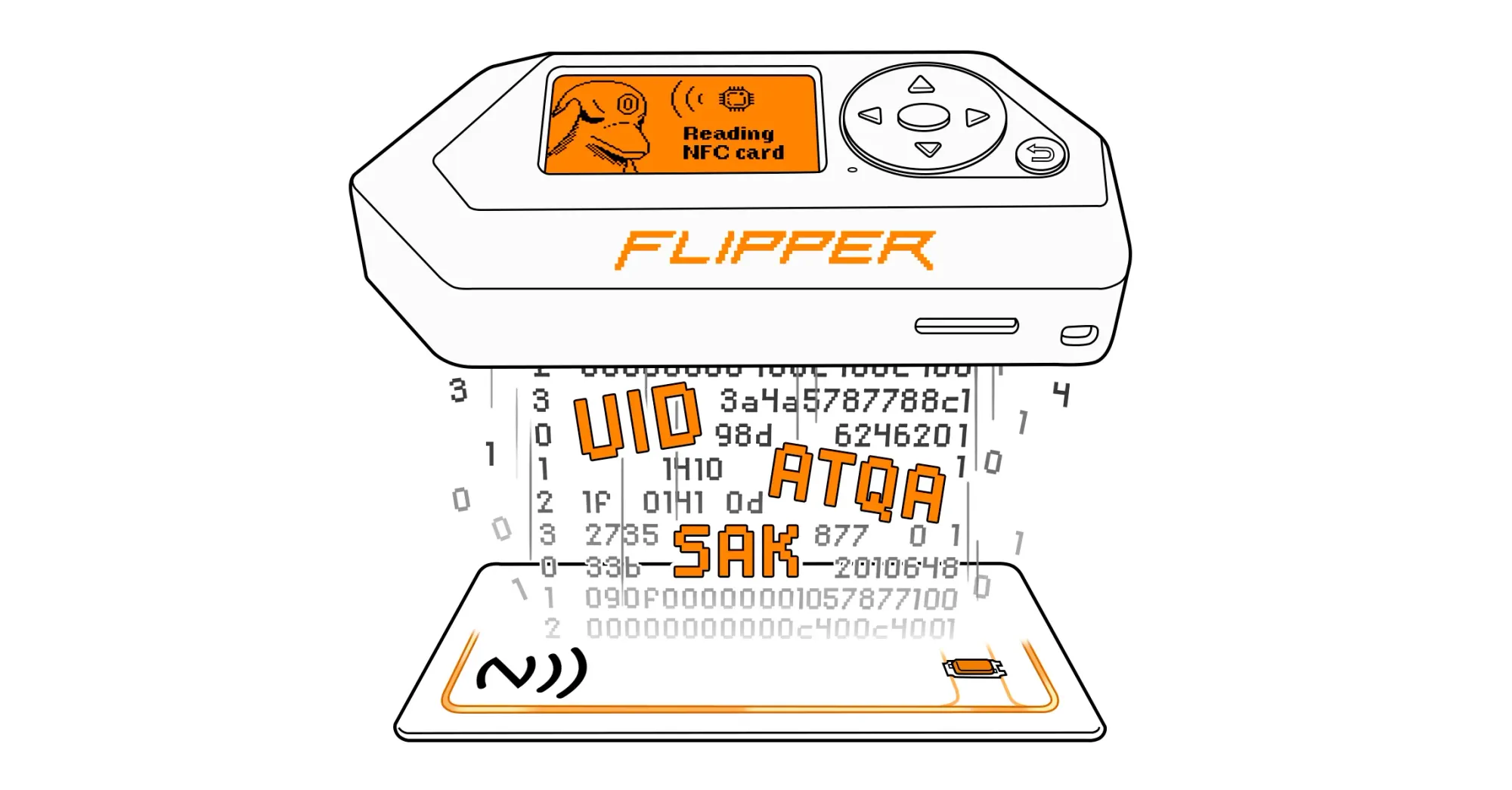
🐬 Flipper Zero: The IoT Swiss Army Knife
The Flipper Zero became an internet sensation for a reason. It’s portable, easy to use, and fun.
- Handles RFID, NFC, Sub-GHz remotes, IR, Bluetooth basics.
- Great for demos and beginner experiments.
- Supported by a massive hobbyist community.
- Limitations: lacks the depth and precision needed for professional pentests.
💰 Price: ~$170
🔋 Multimeter: The Most Overlooked Tool
Before you connect anything, you need to know if a board is alive. A $15 multimeter lets you:
- Measure voltages.
- Identify ground and VCC pins.
- Check continuity.
- Troubleshoot power issues.
It’s simple, but essential.
🔧 Basic Soldering Iron: Your First Hardware Hack
You’ll need to solder headers to connect to UART/JTAG.
- $20 soldering irons are fine for learning.
- Add flux, solder wick, and a bit of patience.
- Upgrade later to a station with adjustable temp.
📡 Cheap Logic Analyzer
Want to see how chips are talking to each other?
- A $20 Saleae clone connects to your laptop.
- Use PulseView to decode UART, SPI, I²C signals.
- First step toward real hardware hacking.
🖥️ Your First IoT Target
Don’t start with a Tesla. Buy cheap IoT gear to practice on:
- Smart plugs (~$10).
- Wi-Fi IP cameras (~$25).
- Old routers (often free).
👉 Real hardware > theory.
✅ Beginner Budget (~$200): Flipper Zero + multimeter + soldering iron + logic analyzer + a device to hack.

🔧 Intermediate IoT Pentesting Toolkit ($600–$800)
Once you’ve learned the basics, you’ll want to expand into wireless and professional RFID attacks.
📡 HackRF One: Your First SDR
A Software-Defined Radio (SDR) is one of the most versatile IoT penetration testing tools.
- The HackRF covers the frequency range of 1 MHz to 6 GHz.
- Lets you capture and transmit signals across the IoT spectrum.
- Perfect for garage door remotes, Sub-GHz sensors, and Bluetooth experiments.
- Massive community + tutorials.
- Limitation: half-duplex.
💰 Price: ~$300
Mini-demo you can try: Capture your garage remote signal, replay it, and watch the door open. That’s SDR power.
🪪 Proxmark3 RDV4: The Professional RFID Tool
If Flipper Zero is a toy, Proxmark3 is the real deal.
- Used by professionals to clone/copy badges.
- Supports high/low-frequency cards.
- Ideal for corporate pentests (building access).
- Steeper learning curve, CLI-focused.
💰 Price: ~$300
👉 Example: In one pentest, an attacker used Proxmark to clone a company’s access badge in under 2 minutes.

🔌 Bus Pirate / Shikra: Talking to Chips
Debug interfaces (UART, SPI, I²C) are the backdoors of IoT devices.
- Bus Pirate/Shikra boards let your laptop “speak” those protocols.
- Use them to dump firmware or modify device memory.
💰 Price: ~$40–$60
🔥 Upgraded Soldering Station
If you’re a frequent solderer, invest in serious gear.
- Adjustable temperature.
- Swappable tips.
- Stable heat control.
Popular: Hakko FX-888D, Pinecil V2, TS100.
💰 Price: ~$100
💻 Firmware Analysis Tools (Free)
Software is half the battle. Learn:
- Binwalk → extract firmware.
- QEMU → emulate binaries.
- Ghidra → reverse engineer code.
- Radare2 → alternative RE.
✅ Intermediate Budget (~$700): HackRF + Proxmark + Bus Pirate + soldering station + firmware tools.
🚀 Advanced IoT Pentesting Lab ($2,000+)
If you’re serious about research, teaching, or consulting, this is your next level.
📡 LimeSDR / USRP: Pro SDRs
When HackRF isn’t enough:
- LimeSDR Mini ($600–$800): full-duplex SDR.
- USRP B200/B210 ($1,100+): academic & enterprise standard.
Unless you’re a researcher, these are overkill.
🔍 JTAGulator
- Auto-detects JTAG/UART pins.
- Saves hours of probing with a multimeter.
💰 Price: ~$200
🔥 Hot Air Rework Station
- Safely desolder chips.
- Essential for chip-off attacks (dumping NAND flash).
💰 Price: ~$200
📈 Oscilloscope
- Visualize power and signal waveforms.
- Useful for debugging & side-channel analysis.
- Not needed for beginners.
💰 Price: ~$400+
📦 Device Collection
By this stage, you’ll want shelves full of devices:
- Smart locks.
- Doorbells.
- Automotive ECUs.
- Medical devices.
Real pentesters need real targets.
✅ Advanced Budget ($2,000+): LimeSDR/USRP + JTAGulator + oscilloscope + hot air + device shelf.
📊 Tool Comparison Tables
Flipper Zero vs Proxmark3
HackRF vs LimeSDR vs USRP
Soldering: Iron vs Station
🚦 Common Beginner Mistakes
- Buying too much gear too soon. → Don’t buy a USRP if you’ve never used HackRF.
- Skipping the multimeter. → Cheap but critical.
- Not isolating test devices. → Never pentest IoT devices on your production Wi-Fi.
- Collecting tools, not skills. → A Flipper with no methodology is just a toy.
📡 IoT Protocols 101
Here’s a quick cheat sheet of protocols and which tools apply:
- RFID/NFC → Flipper, Proxmark.
- Wi-Fi → Alfa adapters, HackRF.
- Bluetooth LE → Ubertooth, HackRF.
- Zigbee/Sub-GHz → HackRF, Flipper.
- Debug (UART/JTAG/SPI) → Multimeter, Bus Pirate, JTAGulator.
❓ FAQs
Is Flipper Zero legal? Yes, but how you use it matters. Don’t clone access badges you don’t own.
Do I need an oscilloscope? Not for beginners. Only for advanced hardware debugging.
Can I practice on my own smart home? Yes, but better to buy extra cheap devices to avoid bricking your daily gear.
🎯 Conclusion: Stop Collecting, Start Hacking
It’s easy to get lost in tools. But here’s the truth:
- You can start IoT pentesting with $200.
- Each upgrade unlocks new attack surfaces.
- Tools don’t hack — your methodology does.
👉 If you’re ready to go beyond collecting gadgets and actually learn to use them in real IoT pentests, check out my IoT Pentesting Course.
Inside, I’ll walk you through hands-on labs with Flipper, HackRF, Proxmark, and more — so you’ll not only know what to buy, but how to use it responsibly.





